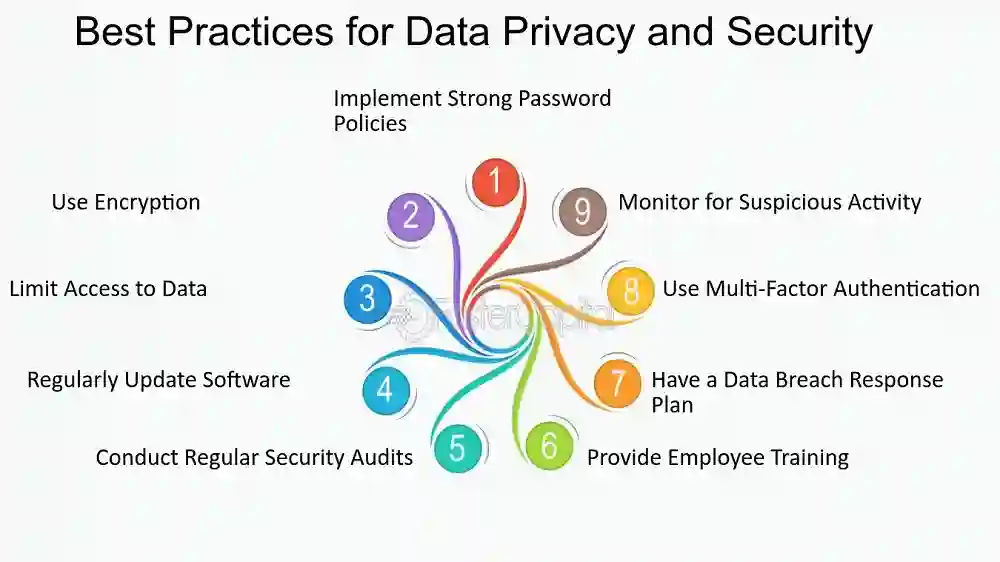
How to Secure Customer Data Without Violating Privacy Laws
In today’s Data advanced world, businesses handle endless sums of client information, making information security a basic concern. Damaging security laws can have genuine results, counting strong fines and misfortune of customer believe. Understanding how to secure client information without abusing security laws is basic for keeping up legitimate compliance and defending your business’s notoriety. This article investigates viable ways to secure client information whereas following protection regulations.
1. Get it the Key Security Laws
To maintain a strategic distance from abusing protection laws, businesses must familiarize themselves with the pertinent controls administering information security. The most well-known security laws include:
- General Information Security Direction (GDPR): This European Union control administers how businesses collect, prepare, and store individual information. It emphasizes getting assent from clients and guaranteeing transparency.
- California Customer Security Act (CCPA): This law secures the security rights of California inhabitants, giving them control over how businesses utilize their individual data.
- Health Protections Movability and Responsibility Act (HIPAA): This U.S. direction is centered on ensuring therapeutic data and guaranteeing secrecy in healthcare-related industries.
By understanding these laws, you can guarantee compliance and maintain a strategic distance from any unintended infringement of privacy.
Why It’s Important:
Not knowing the pertinent protection laws can lead to inadvertent infringement. Understanding these laws is the beginning step to guarantee your trade remains in compliance.
2. Collect As it were Vital Data
When collecting client information, it’s pivotal to follow to the guideline of information minimization. This implies as it were collecting the information that is completely vital for your trade operations. Dodge collecting over the top data that is unimportant to your administrations or items. By doing so, you decrease the chance of damaging protection laws and minimize introduction in the occasion of a information breach.
Why It’s Important:
Over Collecting client information can lead to pointless dangers and security infringement. Restricting information collection makes a difference guarantee that as it were basic data is put away and processed.
3. Get Unequivocal Consent
One of the key standards of security laws such as GDPR is getting express assent from clients some time recently collecting their information. You must illuminate clients around what information you’re collecting, how it will be utilized, and how long it will be put away. Give them with a clear and available way to opt-in and opt-out of information collection processes.
Why It’s Important:
Getting unequivocal assent is not as it were required by law but moreover makes a difference construct believe with your clients. Guaranteeing straightforwardness in your information collection prepare makes a difference: you dodge damaging security laws and sets up validity with your audience.
4. Actualize Strong Information Security Measures
To avoid unauthorized access to client information, execute solid information security measures. This can incorporate scrambling delicate data, utilizing secure passwords, and utilizing firewalls and antivirus computer program. Routinely review your information security frameworks and guarantee they meet the required benchmarks to maintain a strategic distance from potential vulnerabilities.
Why It’s Important:
Information breaches are one of the most common ways businesses abuse protection laws. Ensuring client information with strong security measures decreases the chance of introduction and guarantees compliance with information security regulations.
5. Constrain Information Access
Access to client information ought to be limited to authorized staff as it were. Execute role-based get to controls, where representatives can as it were get to the information vital for their particular assignments. Routinely audit and overhaul get to controls to guarantee they stay in line with your company’s security protocols.
Why It’s Important:
Restricting get to to touchy information makes a difference minimize the hazard of inadvertent or malevolent information spills. It’s moreover a best hone in complying with protection laws by guaranteeing that as it were those with a true blue require can see or oversee client information.
6. Guarantee Information Maintenance is Limited
Another way to remain compliant with security laws is by building up clear information maintenance arrangements. Information ought to as it were be put away for as long as essential to fulfill the trade reason it was collected for. Once the information is no longer required, it ought to be safely erased or anonymized. Holding pointless information increments the chance of damaging security laws and uncovered the trade to potential breaches.
Why It’s Important:
Over-retaining client information can abuse protection laws, which frequently stipulate that individual data ought to not be kept longer than essential. Executing a maintenance approach guarantees compliance and decreases the chance of information misuse.
7. Frequently Survey and Upgrade Protection Policies
Your protection approaches ought to reflect current hones and laws. Frequently survey and upgrade these approaches to guarantee they adjust with advancing security controls. Make beyond any doubt that any changes to your security hones are communicated clearly to your clients, and permit them to audit the unused terms.
Why It’s Important:
Upgrading your security arrangement frequently makes a difference keep up compliance with changing laws and controls. It too keeps your clients educated approximately how their information is being utilized, cultivating believe and transparency.
8. Teach Representatives Approximately Protection Laws
It’s fundamental to prepare your workers almost the significance of information security and the legitimate commitments related with it. Guarantee that everybody included in dealing with client information gets it the centrality of security laws and the steps they must take to guarantee compliance. This preparing ought to be upgraded routinely to reflect unused laws and security practices.
Why It’s Important:
Representatives are frequently the to begin with line of defense against information breaches and protection infringement. Giving customary preparing makes a difference decrease human blunder and guarantees that your whole group is on the same page with respect to information protection.
9. Utilize Secure Communication Channels
When sharing client information inside your organization or with third parties, continuously utilize secure communication channels. Maintain a strategic distance from sending touchy data by means of unsecured mail or decoded stages. Instep, utilize scrambled communication strategies, such as secure e-mail administrations or collaboration apparatuses, to secure the information in transit.
Why It’s Important:
Decoded communication increments the hazard of information being capturing or spilled. Utilizing secure communication strategies guarantees that client information remains ensured amid exchanges and complies with protection laws.
10. Screen and React to Information Breaches
Even with the best security measures in put, there’s continuously a hazard of a information breach. In the occasion of a breach, it’s basic to have a reaction arrange in put. Inform influenced clients instantly, examine the cause of the breach, and take remedial activities to anticipate future episodes. Depending on the seriousness of the breach, you may be lawfully required to report the occurrence to authorities.
Why It’s Important:
A quick and straightforward reaction to a information breach can minimize harm and illustrate your commitment to ensuring client information. Following to breach notice laws is a imperative portion of remaining compliant with protection regulations.
Conclusion
Securing client information without abusing protection laws requires a commitment to straightforwardness, security, and legitimate compliance. By understanding security laws, actualizing solid information assurance hones, and teaching your workers, you can guarantee that your commerce remains on the right side of the law. Taking after these steps will offer assistance ensure your customers’ delicate data and keep up their believe in your commerce. Keep in mind, a proactive approach to information security is key to dodging infringement and cultivating long-term victory.